how to
Water, Lemon Juice, Vinegar, or Nothing: Should You Even Bother Rinsing Chicken?


how to
How to Roll Sushi — The Ultimate Guide

how to
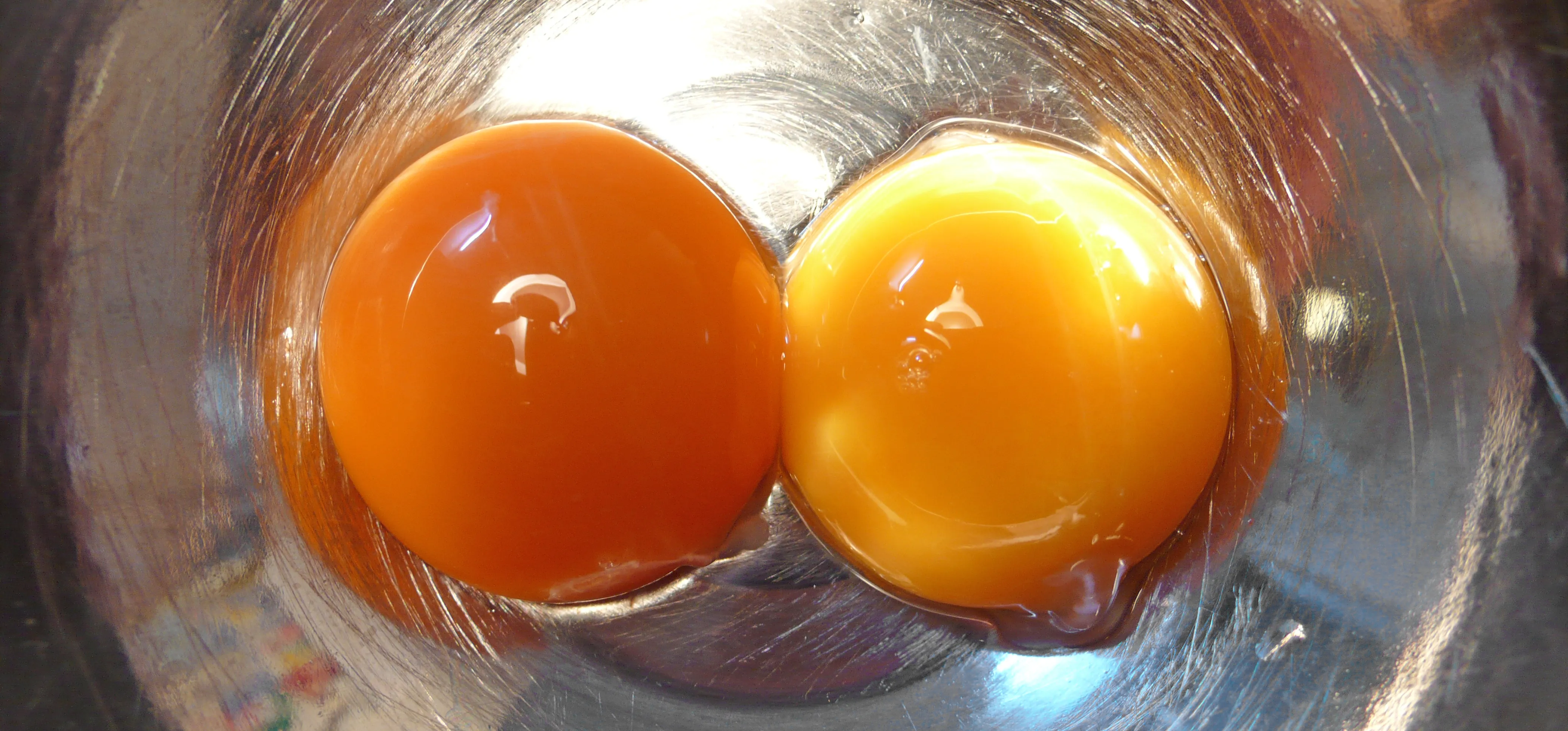
How to Tell if Your 'Expired' Eggs Are Still Good to Eat

I got a Xbox 360 elite and cant find hot to remove the Front USB ports cuz i got it from a Friend and he said if i could fix it by removeing the front USB ports then i could have it. He said that it shorts out the Xbox and i cant find any videos or Tutorials to fix it. Can anyone Help me out plz?


This how to is to help you keep yourself protected from becoming hacked. With 91% of cyber attacks starting with email you have to be keep yourself safe.

I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012.

Introduction: This thread is about sharing your computer security set up. Doing so enables computer beginners choose a good security method to use. It may also benefit intermediate to advanced users depending on the responses this thread receives.

forum
HTTPS Everywhere Just a quick update in regards to HTTPS Everywhere.

This article will be about setting up a static IP (Internet Protocol) address in Windows 7. To see whether you should set one up, ask yourself the following:

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power to...

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping your desktop clean and clutter free, along with the use of software to find documents you have misplaced.

How many Facebook friends do you have? The average person on Facebook has around 140 friends while some hit the ridiculous Facebook friend limit of 5,000. Facebook states that its services are for people you know in person. I don't think anyone has 5,000 friends in person, do you? Personally, I don't even think Megan Fox has 5,000 friends in person, so how could any regular person have that many? But that's beside the point.

I plan on making a big list of software that will work on a Windows machine. It will eventually be huge! But in order for it to become big we must work as a community and share all our free favorite programs. Rules:- The same program cannot be mentioned more than once; - ALL programs must be free in order to advertise it here; - The links and programs must be free; - All programs on here must be 100% legal. Encryption is an exception - but everyone must find find out whether it is legal in...

Hello everyone!

forum
World changes UPDATE: INFOSECURITY WORLD IS NOW KNOWN AS WIRE STORM TECHNOLOGIES.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?

This tutorial will be based on creating a partition in Windows Seven. I have seen so many people attempt to do this themselves without guidance. Ultimately, they end up with a corrupt system. The aim of this tutorial is to make sure you don't corrupt your system.
Featured On WonderHowTo:
Productivity & Shortcuts

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when...

Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to download it to you can refer to this manual when you are experiencing connection issues. I would also like to note that the manual has been loaded onto a free server - it will remain on the server until people stop...

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it is a real pain.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.
Featured On WonderHowTo:
Music & Audio

Hello and welcome to yet another InfoSecurity World tutorial. This post is based on the Windows 7 'GodMode' panel. Windows 7 comes with many hacks, cheats and tweaks. This bonus lesson will teach you how to create Windows 7 GodMode.

It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Hello, welcome to my first post!

The purpose of this article is to discuss how you can change your Windows 7 logon screen. This post will explain how to require a user to enter a username and password by default like the classic version of Windows.

Merry Christmas all!
Featured On WonderHowTo:
Augmented Reality

Hi everyone,

This article relates to changing the settings in Adobe Flash so that you can improve your overall computer security and privacy. Changing these settings might have a negative performance impact on your computer - but it is worth while.